Cybercrime Attacks
- Beyond zero trust computing
- Even with system intrusion attacks hackers are unable to access the confidential data
- Quantum secure
Fully Homomorphic Encryption
Data remains encrypted during storage, transit and processing
Perform arbitrary calculations including AL/ML models without disclosing the underlying confidential plaintext data
Third-Party – Business Enhancement
- What if you could share your data without disclosing it?
- Share and monetize data without disclosing the confidential plaintext data
- Data as a valuable asset for business efficiency
Compute Intensive
1 million X performance acceleration required for real-time FHE
Cornami uniquely scales to achieve real-time FHE meeting market performance, power and cost requirements for commercial adoption
Reduce Business Risk
- Privacy compliance
- Regulatory compliance
- Reputation and lawsuits
- Operational risk – internal
Fully Homomorphic Encryption – The Holy Grail of Data Security
Delivers quantum-proof data privacy while enabling market Intelligence for our data-driven economy
Beyond Zero Trust Computing
Today’s, perimeter-based, security techniques are built with thousands of integrated hardware and software components that are constantly changing with bug fixes, feature updates, and module replacements. This reality statistically guarantees that, regardless of effort, computing infrastructure attack points always exist with the only issue being whether they have already been identified and exploited or you just don’t know about it yet.
It is Impossible to Guarantee:
- Hack proof firewalls
- Secure operating systems
- Computer chips without embedded trojans
- Exposure risk from employees/contractors
Assume the computing environment is compromised
The US government among others take the stance of Zero Trust that you need to assume the computing environment is not secure and at risk for breach.
Protect the Data
FHE provides quantum-secure, privacy-preserving computing on encrypted data sets, guaranteeing that data and its derivative computational results remain secure from modification and/or breach despite compromised computing infrastructure.
The Problem
To date, although highly desirable, FHE is too computationally intensive to be commercially viable with current technologies.
Cornami Delivers Real-Time FHE
Cornami’s unique Post-von-Neumann TruStream® scalable architecture achieves 1 million x acceleration for real-time FHE
TruStream® Reconfigurable Compute Fabric
Scales linearly with number of cores all transparent to the software to hit performance requirements.
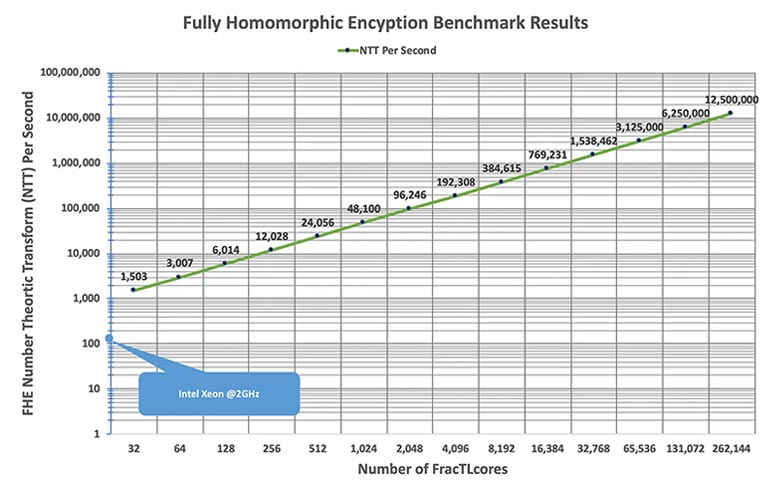
Real-time FHE is a game-changer for data security
- Secures data from breach / modification throughout its lifecycle
- Application services that maintain data confidentiality
- Analysis of confidential data aggregated from multiple parties
- Support PPML (Privacy Preserving Machine Learning) models without ever decrypting the data
- Private Set Intersection (PSI): secure and confidential data intersection check within a larger database
- Guaranteed data security and integrity across sensor – controller – actuator real-time control chain
- Application confidentiality executing on untrusted platforms
- Monetization and sharing of confidential data for business enhancement and market intelligence


